Bad people are trying to take over your YouTube channel right as you read these words. They want access and control to either destroy all of your hard work, or use your channel’s reach and subscribers to promote an illegal scam.
Imagine if all of your hard work and growth on YouTube was taken away in an instant… It would be devastating.
If you think I’m being overdramatic right now, I promise I’m not. It happens every single day to YouTube channels, even huge ones with millions of subscribers like Corridor Crew or Linus Tech Tips.
Even my much smaller channel (that still generates $20,000 per month) has people trying to access or steal it several times a week.
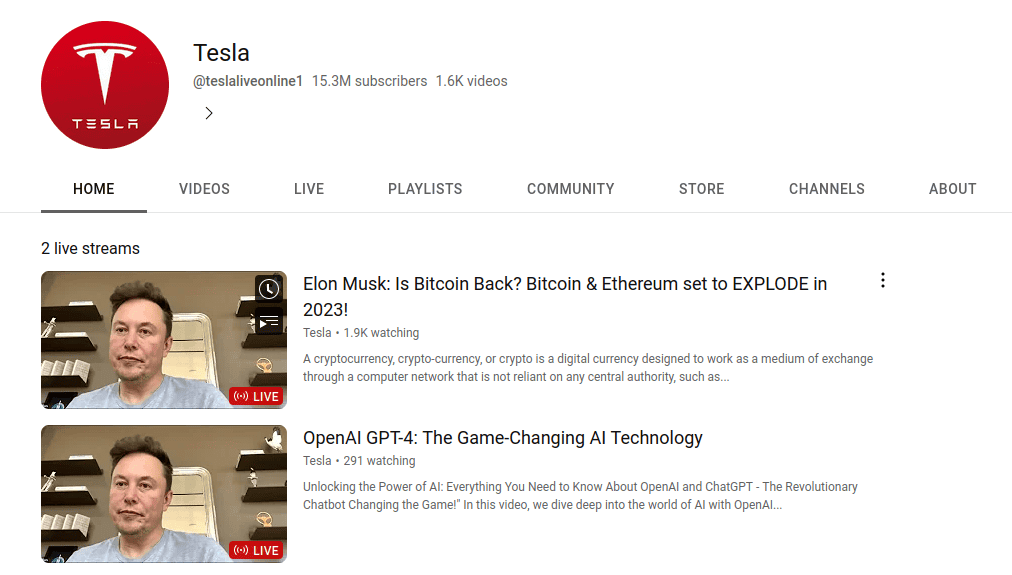
Don’t believe me? Here’s an email I literally received while writing this article:

If I had clicked that link highlighted in red and downloaded the sponsor’s “promotional materials” – boom. My entire channel is gone.
So, I set out to discover the best ways to keep my YouTube channel secure and protect it from hackers and scammers.
The good news is that it’s easier than you think.
In this article I’ll take you through the step-by-step process you need to do RIGHT NOW to secure and lock down your account, and protect it from who I like to call “Johnny Hacker” (apologies in advance if your name is Johnny, I’m sure you’re a nice guy and not a hacker).
These are also the exact same protocols I use on my own YouTube channels.
How can my YouTube account get hacked?
Firstly, I want to discuss exactly how someone can gain access to your YouTube channel. There are two main methods:
- Gaining access to the email account linked to your YouTube account
- Browser hijacking (specifically session hijacking) via malware
Both of these methods have disastrous results. The hijacker will have full control over your YouTube channel and can delete videos, change the channel name, livestream an illegal scam, or even simply delete your channel altogether.
If you’re a big, successful channel, typically YouTube can help you regain access and recover and “rollback” your channel to a previous point in time.

But – sometimes the damage has already been done, and if you’re a smaller channel, you may not have the same level of support from YouTube as the larger ones. As the saying goes – an ounce of prevention is worth a pound of cure. It’s simply better to just avoid getting hacked in the first place.
Pro tip: If someone does gain access to your channel and you’re not having much luck with traditional account recovery methods, you can message Team YouTube on X/Twitter.
So, let’s talk about these two methods that can be used to access your channel in more detail.
1. Gaining access to the email account linked to your YouTube channel
This one is pretty self-explanatory. To create a YouTube channel, you need to have a Google account. This Google account can be either a gmail.com email address, or an email address from another provider e.g. outlook.com.
If someone gains access to this email account, they can reset or recover the password for your YouTube account. The reset link will just come straight through to your email inbox – which they’re currently inside.

Gaining access to an email account is actually quite easy if the owner of that account has been lazy and hasn’t secured it properly. For example:
- Not using a Password Manager to create and store strong passwords
- Using the same password on multiple online accounts
- Not using two-factor authentication
Don’t worry, I’ll teach you how to take care of this later on.
2. Browser/session hijacking
This is by far the scariest method, and scared the sh*t out of me when I first heard about it. Microsoft explains browser hijacking better than I can, but essentially it’s a piece of malware that’s designed to “steal” or “hijack” the data in your browser.
Websites like YouTube will store little pieces of data in your browser known as “cookies”. These cookies (weird name, I know) are used by websites to tell if you’re logged in or not, among other things. Otherwise, whenever you visit a website you’d have to log in every single time – which is annoying.

Browser hijacking (or specifically, a process called “session hijacking”) exploits this to completely bypass the login process and gain access to your YouTube channel.
It hijacks your current active YouTube “session”.
Once your computer/browser is infected, the attacker can simply navigate to YouTube and will be logged into your account – as if they’d just logged in using your email address and password.
This is how huge channels like Corridor Crew and Linus Tech Tips were hacked.
Step 1: How to secure your YouTube/Google account
Now that you know the two main methods of how Johnny Hacker can gain access to your account, let’s start to lock everything down. Starting with the account you use to log in to your YouTube channel.
1. Use a separate email account
It’s best practice to use a separate email account for your YouTube channel. This email account is ONLY used for logging in and out of your channel and nothing else.
For example, I would not use my personal first.lastname@gmail.com email account. I would create a new account, something like channelnameprivate@gmail.com.
Bonus points – buy a custom domain from a website like Namecheap and use an email hosting provider like Fastmail to set up your own branded email account. It’s easier than it sounds, trust me, and it only costs a few bucks a month.
This looks incredibly professional when brands or sponsors reach out to you via email. Instead of “channelnamebusiness@gmail.com” it will be “liam@channelname.com”.
I use this method along with some other ones to secure roughly $5000-$12,000 worth of sponsor revenue per month.
Note: Don’t use your YouTube login email to communicate with anyone other than YouTube support (and of course logging into your YouTube channel). More on that later.
2. Use a password manager and create a new, complex password
I personally use 1Password, although any reputable password manager will work. Bitwarden is good too and is free. The most important thing is to create a password that cannot be guessed and is UNIQUE – do not use it anywhere else EXCEPT for your YouTube channel.

Don’t write your password down on a piece of paper, don’t put it in a Word document on your computer, don’t try to remember it in your head – USE A PASSWORD MANAGER!
Ok, phew. Sorry about that, I get a little worked up over passwords. My university thesis was on data security so it’s a passionate topic.
This step is so important because so many people use the same password on every website. What happens when one of these websites inevitably gets hacked, breached, or has a data leak? That’s right, your password (and whatever email address you used) is now available on the internet in an Excel file to be downloaded by Johnny Hacker.
Pro tip: You can also check if any of your email addresses have been in a data breach.
3. Use two-factor authentication (2FA)
I won’t go into too much detail here – you know what 2FA, or two-factor authentication is. You know those 6 digit codes you sometimes have to enter when logging in? That’s it. There’s a new kid on the block too – called Passkeys.
Whatever method you end up using, just make sure you search how to set it up on whatever email account or Google account you use (try to stay away from email and SMS authentication, they are notoriously insecure).

Two-factor authentication is an incredibly important tool to prevent phishing attempts. You know, when you get sent dodgy emails asking you to “log in” to a fake website that isn’t actually that website at all and is some guy trying to steal your account.
Even if you fall for a phishing attack, often the attacker is stopped because they don’t have your “second” factor of authentication e.g. a 6 digit code.
That’s where this next recommendation comes in…
4. The nuclear option – hardware security keys
This is what I personally use to secure all of my most important online accounts – PayPal, YouTube, Google, email, bank account etc.
A hardware security key is exactly what it sounds like. It’s essentially a little USB device that needs to be physically plugged into your computer or phone in order to log you in (on top of entering your secure, unique password).

So even if an attacker had my email address and my password, they would still need PHYSICAL access to my security key. Which is impossible, unless they’re also standing in my room with a gun pointed at me… In that case, you can have my YouTube channel bro!
Is it overkill? Maybe, but seeing as a single one of my YouTube channels generates me $200,000+ USD per year, I’ll do everything I can to keep it secure.
I personally use a Yubikey. You can buy various types, I have a normal USB-C and USB-A one and also a tiny little one that slips nicely into my MacBook (you can see it in the photo above). Some of them are NFC too so they can simply be tapped against your phone.
Step 2: How to prevent browser hijacking
Ok, now that we’ve dealt with the easy stuff and your YouTube channel is nice and secure, let’s talk about browser/session hijacking.
Yes, even if you follow ALL of the previous steps, including using a hardware security key, browser hijacking can still happen.
At the time of writing this, there’s one main method hijackers use.
They’ll send you an email masquerading as a sponsor, or a brand, or a company. The contents of the email differs. I’ve had some pretend to be major brands, or game developers, or an agency working on behalf of a brand that wants to sponsor one of my videos.
Often these emails can look pretty legit too – the hijackers will use proper logos, the domain the email is sent from might look fine at first glance, and some of them are well-written.
These are often NOT your typical crappy spam/phishing attempts that you may see in your personal email accounts.
What a browser/session hijack attempt looks like
One thing to mention is that the sophistication of these hijacking attempts may vary based on how “valuable” your channel is. If you’ve got a larger channel, you can bet Johnny Hacker is going to pull out all the stops and try his best to get you.
My first experience with a potential browser hijack attack nearly got me. It was very well designed.
I received an email asking me my rates for a 60s sponsored segment featuring a product that I had heard about. I didn’t get any immediate red flags, they were even using what seemed like a legit domain. We exchanged a few emails over several days, agreed on talking points and a price, and everything seemed normal at that point.
Unfortunately I don’t have the original email thread anymore. Luckily, as I was writing this very article, a new session hijack attempt came through, so I played along to get some screenshots for you.

You can see in the email above it’s the same strategy – they’ll wait until a few emails have been sent back and forth between you and them. This is all an attempt to trick you and build a false sense of security.
Then, they send the malware disguised as a Google Drive or Dropbox link.

This will usually lead you to some kind of .zip or even .rar file that’s supposed to contain a contract, or sample videos, or marketing points to cover during the video.
There is of course zero reason to ever send a .rar file. The .zip file type however is more common. Sometimes legitimate sponsors or companies will send a few files at once and it’s easier to send a .zip file with everything rather than a bunch of separate files.
So occasionally what Johnny Hacker will do is make the .zip file size huge, like one gigabyte (1 GB) in size, when it should be a few megabytes (4-15 MB) at most if it’s a legitimate interaction.
Johnny artificially makes the file size so big because large files are difficult for antivirus programs to properly scan, so users will skip that step and just open the file – infecting their computer.
So, how do you prevent against this kind of attack?
1. Verify the interaction
Use your gut feeling – if something feels off, it probably is. Is the email poorly written? Is the offer too good to be true? For example wanting to pay your small 400 subscriber channel $2000 for a 60s sponsored segment?
Often the email domain will reveal the true nature of the sender. If they claim they’re Manscaped for example, but their email domain is some weird combination of letters or it’s “manscapedmarketing@gmail.com” then it’s probably fake.
Make sure you actually click on the contact name and look at their email. Most email clients will hide them by default and just display their contact name (in the screenshots of scam emails I’ve included on this article, I manually added the email in the screenshot, otherwise you wouldn’t have been able to see it).
You can also search the email address. If it’s listed on their official website, you’re probably ok.

The above photo is a good example of a crappy attempt at a potential browser hijack.
Note the weird email address, the weirdly formatted text content, and the context. This was sent to a tech review channel (mostly viewed by men), but Zara is a fashion brand for women. Why would they want to advertise on this channel? Red flag.
If all else fails and you’re just not quite sure, ask them to verify themselves.
A simple “Hey, could you please send me a message from your official company X/Instagram/Snapchat/email account so I can verify you? I’ve received a lot of phishing emails recently so I just want to make sure.” works fine.
Any legitimate company/brand won’t have a problem with this.
If it’s not a company/brand reaching out to you directly and instead it’s an agency acting on their behalf, the same applies. Verify the email, check out their website – do they actually have one? Is it legit? Do they have social media or other creators they’ve worked with?
Pro tip: Many YouTube creator subreddits/Discord channels etc. will allow you to post there and ask if anyone else has worked with that specific agency/brand/company. It can be a good way to find out the legitimacy of some emails.
2. Be careful what you download
I know, this is kind of obvious, but I’ve dealt with hundreds of sponsors over the years and I can tell you that the following files are what they send 99.9% of the time:
- A contract (commonly in .pdf form) that’s usually no more than a few megabytes in size (1-5 MB).
- An additional .pdf or sometimes a .jpeg or .png image that contains talking points or information about their product. This is usually anywhere from 3-15 megabytes (3-15 MB) in size. Sometimes there may be 1 or 2 of these (like a talking points guide, and a manual to update the firmware for example).
- A link to a Dropbox or Google Drive folder containing brand material like logos, product demo videos, or images. You should be able to view these videos/images directly in Dropbox/Google Drive without having to download them.
That’s it. Be very careful about any additional things they want you to download. Never download any weird file extensions either, like .rar
And be EXTREMELY cautious if any of the above files I mentioned are significantly larger than those file sizes.
If you’re on Windows, you can also use the built-in antivirus program Windows Security to scan the downloads before you open them.
Alternatively you can use a free website called VirusTotal to scan the files for potential malware.
If all else fails and you’re just not quite sure, even if you’ve already downloaded the file – simply do not open it. Delete it.
Other tips to further secure your YouTube channel
I’ve covered the two biggest security issues when it comes to securing your YouTube channel. However, there are some other things you should consider.
Don’t use your YouTube email address as the “contact” email address on your channel
Use two separate email accounts. Your contact email address is public and visible to the entire world. Even though you’ll have a strong password and two-factor authentication (at least, I hope you do after reading this article), you still don’t want that email floating around out there, just in case.

Ideally you should have your own custom domain, and something like youtube@yourchannel.com as the email you use to login to your channel, and enquiries@yourchannel.com as the email you display publicly for people to contact you.
Implement good online security practices
Take a moment to look at your online footprint. Do you have random devices (like a phone or iPad) floating around that maybe aren’t password protected or have a pin code?
Do you use a VPN when travelling or using unknown wifi networks?
Do you stay vigilant for other phishing or hacking attempts in your life? Like fake SMS messages or phone calls?
Having good habits is important, because once your channel starts gaining popularity, the volume of emails, brand offers, and scams will increase accordingly. All it takes is for you to slip up one time and you could lose everything.
Use a brand account to manage your channel
You’re more than likely already using a Brand Account with your YouTube channel.
If you are, you have the option to add extra managers to your Brand Account. Usually this is for adding team members or people who help you with the channel, but I personally use it as another layer of security for my channel.
You can access this in your YouTube Studio. Click Settings, then Permissions, then Manage Permissions
I have a “Primary Owner” permission Google account and a “Manager” permission Google account added to my Brand Account.

I only access my channel using my “Manager” permission account. You see in the above image how I only have the option to remove myself and not the Primary owner, or add any new accounts?
That means even if I do fall victim to browser hijacking, the “damage” they can inflict on my channel is somewhat restricted (e.g. they cannot transfer the channel to their own account, cannot delete the channel, and cannot add new users).
Limit other people’s access to your channel
If you have multiple people in your team, or maybe share a channel with someone, use your brand account to delegate their access. For example, you can give them restricted access so that they can only upload videos and nothing else.
This restricts the amount of “attack vectors” Johnny Hacker has. Even if he successfully session hijacks another person linked to your channel – if they don’t have the appropriate level of access, there’s nothing much he can do.
Is My YouTube channel protected now?
Congratulations! If you’ve followed all of my steps, your YouTube channel is about as safe as it can get.
Keep your eyes peeled though – keeping your channel secure is an ongoing process and will require your time and attention.
Consider joining my email list to keep updated with any new hacking, scams, or hijacking techniques.
What should I do if my YouTube channel has been hacked?
If someone gains access to your channel and you’re not having much luck with traditional account recovery methods, you can message Team YouTube on X/Twitter. They will help you recover your channel.





